网站首页 文章专栏 03网络隔离测试.md
03网络隔离测试.md
部署应用
# 创建 production staging 命名空间
kubectl create namespace production
kubectl create namespace staging
# 在每个命名空间各部署一套服务
cd kube-router
wget https://raw.githubusercontent.com/mgxian/istio-test/master/service/node/v1/node-v1.yml
wget https://raw.githubusercontent.com/mgxian/istio-test/master/service/go/v1/go-v1.yml
kubectl apply -f node-v1.yml -n production
kubectl apply -f go-v1.yml -n production
kubectl apply -f node-v1.yml -n staging
kubectl apply -f go-v1.yml -n staging
# 查看状态
kubectl get pods --all-namespaces -o wide
输出
production service-go-v1-6479d45f4-wjhvq 1/1 Running 0 5m16s 10.244.1.66 node02 <none> <none>
production service-node-v1-86d99648-skpmc 1/1 Running 0 5m16s 10.244.2.53 node03 <none> <none>
staging service-go-v1-6479d45f4-gc9qs 0/1 Running 0 9s 10.244.2.55 node03 <none> <none>
staging service-node-v1-86d99648-7lbvj 1/1 Running 0 5m15s 10.244.2.54 node03 <none> <none>
测试pod通信
获取相关POD信息
PRODUCTION_NODE_NAME=$(kubectl get pods -n production | grep Running | grep service-node | awk '{print $1}')
STAGING_NODE_NAME=$(kubectl get pods -n staging | grep Running | grep service-node | awk '{print $1}')
PRODUCTION_GO_IP=$(kubectl get pods -n production -o wide | grep Running | grep service-go | awk '{print $6}')
STAGING_GO_IP=$(kubectl get pods -n staging -o wide | grep Running | grep service-go | awk '{print $6}')
echo $PRODUCTION_NODE_NAME $PRODUCTION_GO_IP
echo $STAGING_NODE_NAME $STAGING_GO_IP
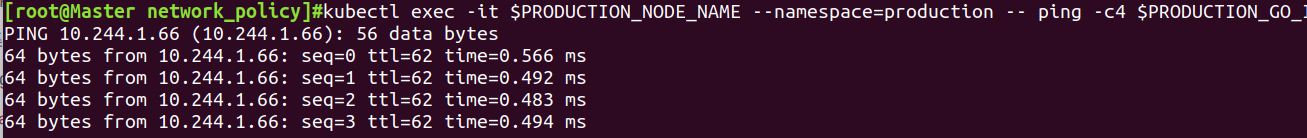
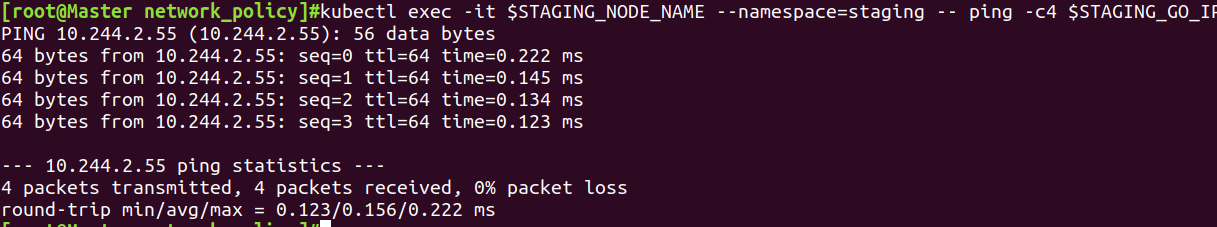
同namespace的pod通信
kubectl exec -it $PRODUCTION_NODE_NAME --namespace=production -- ping -c4 $PRODUCTION_GO_IP
kubectl exec -it $STAGING_NODE_NAME --namespace=staging -- ping -c4 $STAGING_GO_IP
不同namespace的pod通信
kubectl exec -it $PRODUCTION_NODE_NAME --namespace=production -- ping -c4 $STAGING_GO_IP
kubectl exec -it $STAGING_NODE_NAME --namespace=staging -- ping -c4 $PRODUCTION_GO_IP
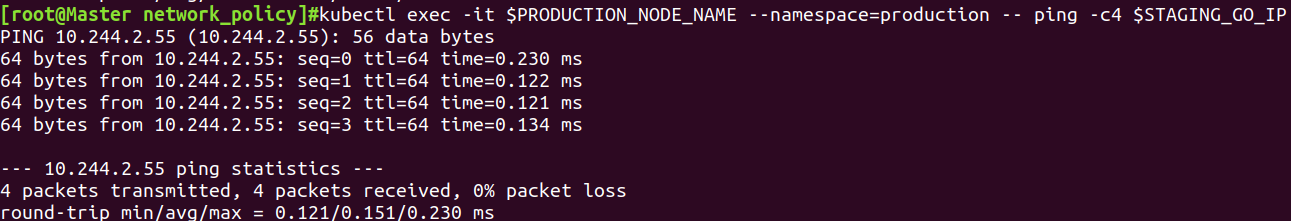
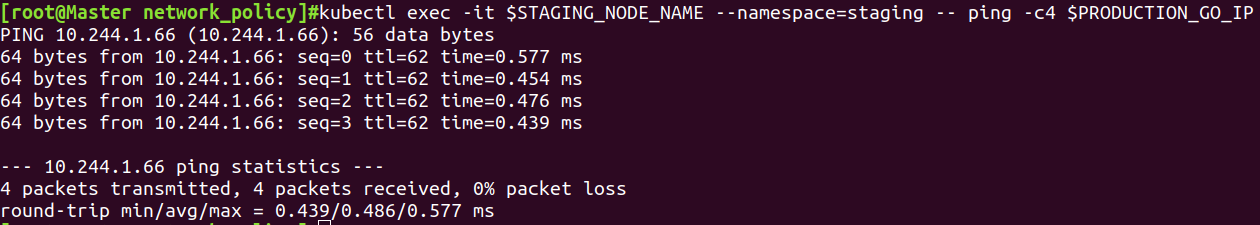
结论:任何namespace的任何pod间都可以直接通信
设置默认策略测试
设置默认策略为拒绝所有流量
cat >default-deny.yml<<EOF
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: default-deny
spec:
podSelector: {}
policyTypes:
- Ingress
EOF
kubectl apply -f default-deny.yml -n production
kubectl apply -f default-deny.yml -n staging
# 测试通信
# 同namespace的pod通信
kubectl exec -it $PRODUCTION_NODE_NAME --namespace=production -- ping -c4 $PRODUCTION_GO_IP
kubectl exec -it $STAGING_NODE_NAME --namespace=staging -- ping -c4 $STAGING_GO_IP
# 不同namespace的pod通信
kubectl exec -it $PRODUCTION_NODE_NAME --namespace=production -- ping -c4 $STAGING_GO_IP
kubectl exec -it $STAGING_NODE_NAME --namespace=staging -- ping -c4 $PRODUCTION_GO_IP
结论:所有pod间都不能通信
设置允许规则
配置
# 设置 service-go 允许从 service-node 访问
cat >service-go-allow-service-node.yml<<EOF
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: service-go-allow-service-node
spec:
podSelector:
matchLabels:
app: service-go
ingress:
- from:
- podSelector:
matchLabels:
app: service-node
EOF
kubectl apply -f service-go-allow-service-node.yml -n production
kubectl apply -f service-go-allow-service-node.yml -n staging
# 设置 service-node 允许 访问 tcp 80 端口
cat >service-node-allow-tcp-80.yml<<EOF
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: service-node-allow-tcp-80
spec:
podSelector:
matchLabels:
app: service-node
ingress:
- from:
ports:
- protocol: TCP
port: 80
EOF
kubectl apply -f service-node-allow-tcp-80.yml -n production
kubectl apply -f service-node-allow-tcp-80.yml -n staging
测试
同namespace的pod通信
kubectl exec -it $PRODUCTION_NODE_NAME --namespace=production -- ping -c4 $PRODUCTION_GO_IP
kubectl exec -it $STAGING_NODE_NAME --namespace=staging -- ping -c4 $STAGING_GO_IP
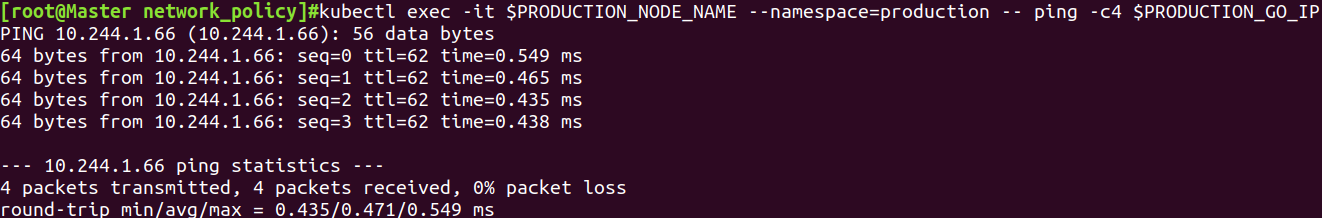
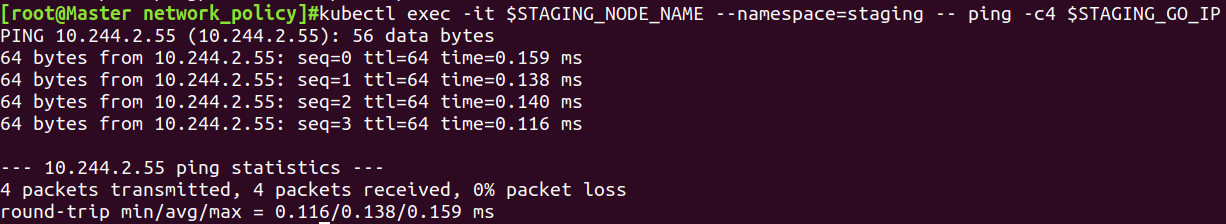
不同namespace的pod通信
kubectl exec -it $PRODUCTION_NODE_NAME --namespace=production -- ping -c4 $STAGING_GO_IP
kubectl exec -it $STAGING_NODE_NAME --namespace=staging -- ping -c4 $PRODUCTION_GO_IP
通过service测试
PRODUCTION_GO_SVC=$(kubectl get svc -n production | grep service-go | awk '{print $3}')
STAGING_GO_SVC=$(kubectl get svc -n staging | grep service-go | awk '{print $3}')
echo $PRODUCTION_GO_SVC $STAGING_GO_SVC
curl $PRODUCTION_GO_SVC
curl $STAGING_GO_SVC
结论:同一namespace的pod间可以通信,不同namespace的pod间不可以通信,只允许配置了网络规则的pod间通信.通过 service 也无法绕过网络隔离策略
清理测试环境
# 删除 namespace 自动删除相关资源
kubectl delete ns production
kubectl delete ns staging
参考:
- k8s使用kube-router网络组件并实现网络隔离
- k8s使用kube-router网络插件并监控流量状态
- Declare Network Policy 使用busybox访问service,值得看看
目录
分类导航
随笔
深度学习
报错解决
效率工具
centos
算法题目
数据结构
未分类
python
网站
书评
docker
书单
2019书单
机器学习
linux
python高阶教程
latex
linux设备
嵌入式
信号与信息处理
影评
django
科普
爬虫
自然语言处理
vue
运维
系统优化
数据库
git
视频
短视频
Go
html
tensorflow
云加社区
单片机
驾考
kvm
gnuradio
markdown
matlab
博客
mysql
nextcloud
vpn
pandoc
pyqt5
vscode
云服务
网络代理
cmake
javascript
vim
网站日常
热门文章